Step-by-Step Fine-Grained Password Policy in Windows 2008
This step-by-step guide shows how to implement Fine-Grained password policy in windows 2008.
Overview of Fine-Grained Password Policy
In older releases of windows (2000/2003) active directory domain you were only allowed to have 1 password policy and 1 account lockout policy both defined in the “Default Domain Policy” and applied to all users in the domain. As a result, you were not able to define different policies to each set of users. As a workaround, Microsoft has released with Windows server 2008 a possibility of having multiple password/lockout policies to allow IT administrators increase security on selected accounts such as financial officers while keeping such measures lighter for ordinary users.
For implementing fine-grained password policies we need to perform the following steps but first we need to define the following requirements.
| Setting | Value |
| Enforce password history | number of passwords to remember |
| Maximum password age | number of days before a password expires |
| Minimum password age | minimum number of days a password should not be changeable |
| Minimum password length | length of password |
| Passwords must meet complexity requirements | Enable/Disable whether password should be complex or not |
| Account lockout duration | Amount of time in minutes |
| Account lockout threshold | Amount of time in minutes |
| Reset account lockout counter after | Amount of time in minutes |
Step by Step Instructions
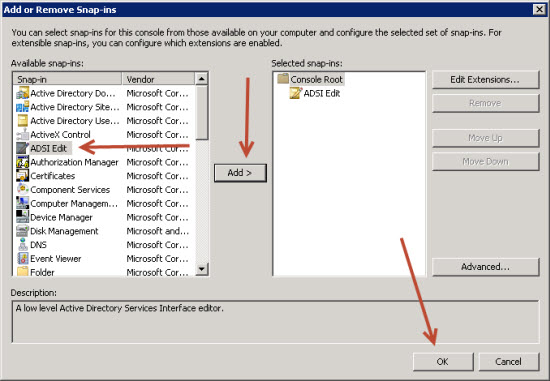
1. Log on to one of your domain controllers and open ADSI Edit snap-in
- Navigate to Start, Run, type MMC.
- From the File menu, select Add/Remove Snap-in…
- Select ADSI Edit, click Add and OK.
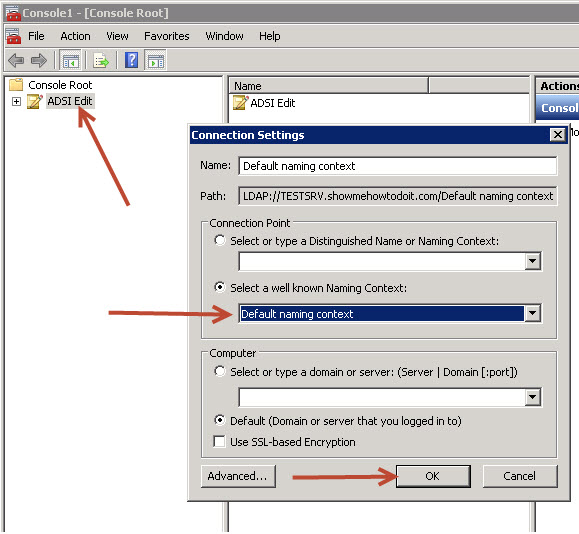
2. In the ADSI Edit snap-in, right-click ADSI Edit, and then click Connect to.
3. In the Name field, enter your domain name, and then click OK. We are going to use showmehowtodoit.com in this example as a reference
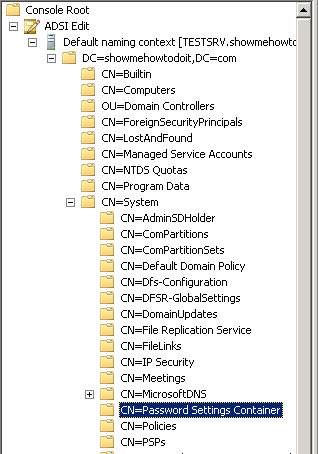
4. Expand the tree all the way down to:
Default naming context [TESTSRV.showmehowtodoit.com] -> DC=showmehowtodoit,DC=com -> CN=System -> CN=Password Settings Container.
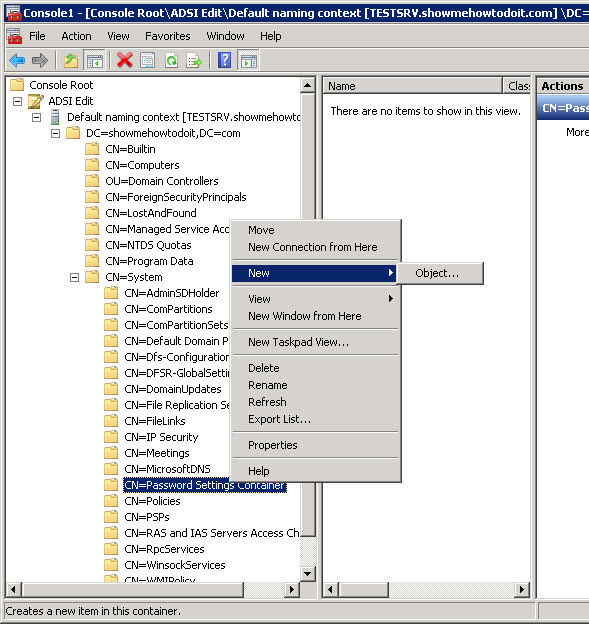
5. Right-click on the container and select New->Object
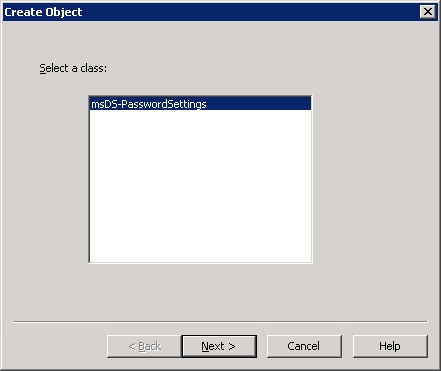
6. In the Create Object dialog box click msDC-PasswordSettings, and then click Next.
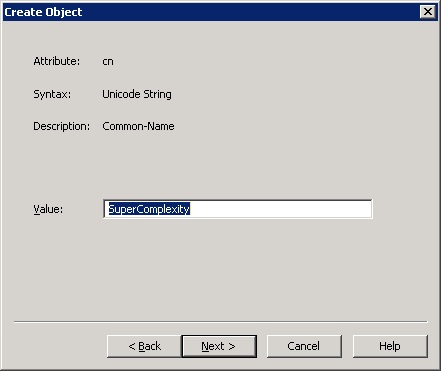
7. In the Create Object dialog box, enter a desired name that will be describing the new password PSO settings. We will use SuperComplexity in this example.
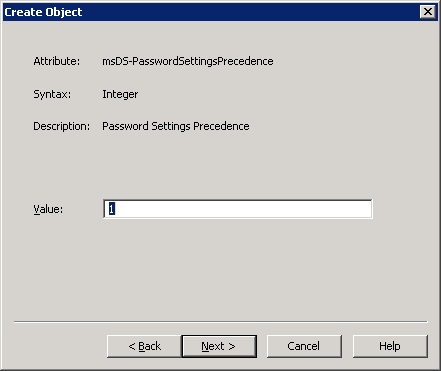
8. For the msDS-PasswordSettingsPrecedence value, enter a value, and then click Next. In this example we will enter number 1. This setting is used to eliminate conflicts in case multiple PSOs apply to the same group at the same time. The lower the value, the higher the precedence that the PSO gains. For example, if a group is about to be assigned the SuperComplexity policy and another policy, the policy with the lowest msDS-PasswordSettingsPrecedence value will apply.
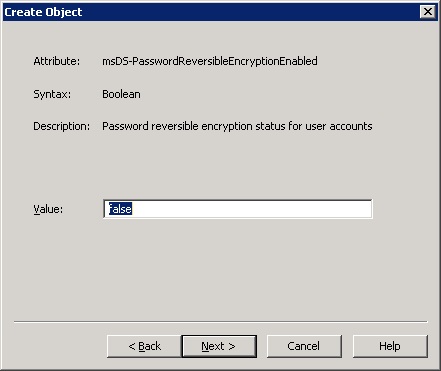
9. For the msDS-PasswordReversibleEncryptionEnabled value, enter false, and then click Next unless you have a particular reason of saving your users’ passwords in active directory in a reversible format (crackable).
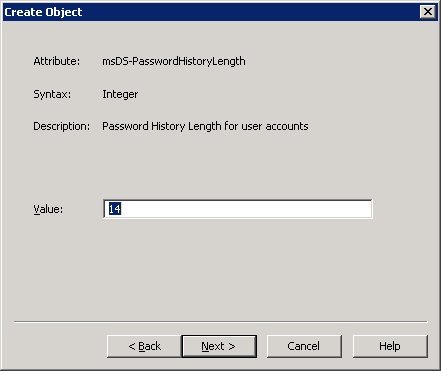
10. For the msDS-PasswordHistoryLength value, enter the number of passwords to be remembered, and then click Next. we will use 14 passwords to be remembered in this example.
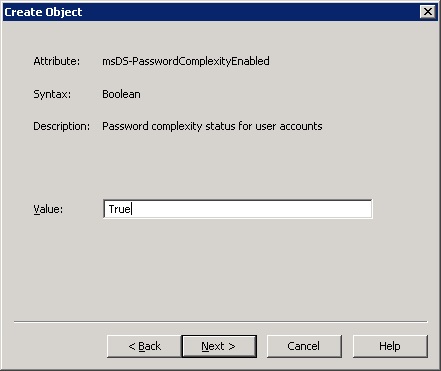
11. For the msDS-PasswordComplexityEnabled value, enter you wish the passwords to be complex or not, and then click Next. We will use True in this example.
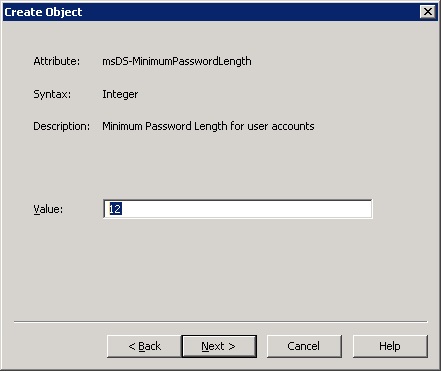
12. For the msDS-MinimumPasswordLength value, enter the minimum length the password should be. We will use 12 for this example.
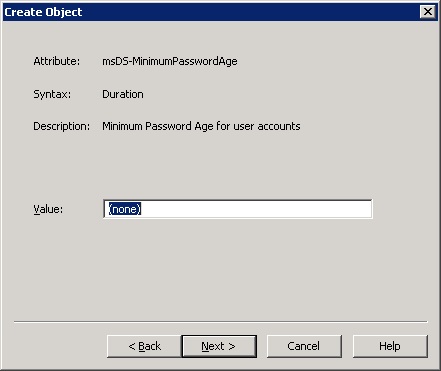
13. For the msDS-MinimumPasswordAge, enter the amount in Time you want the password to be unchangeable, and then click Next. The format should be DD:HH:MM:SS, example 1:00:00:00 for 1 day. In this example we would like to allow immediate change of password if needed, so we will set this setting to (none).
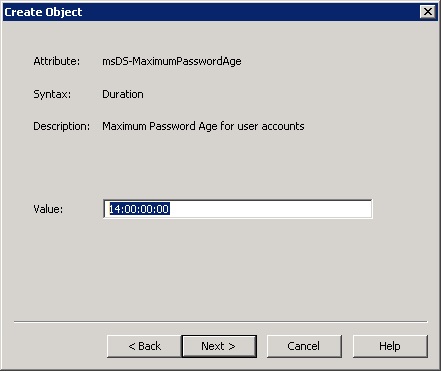
14. For the msDS-MaximumPasswordAge, enter the amount of time that the password will stay valid before expiring. The format should be DD:HH:MM:SS, example 14:00:00:00 for 14 days.
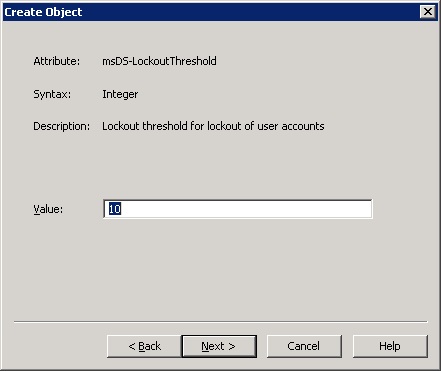
15. For the msDS-LockoutThreshold set the number of times a password is entered wrong before the account gets locked-out in active directory. Be careful, as setting this value to a low value may result to an account lockout storm. We will use 10 (tries) in this example. Keep in mind that any existing users with wrongly cached passwords will lockout really quickly.
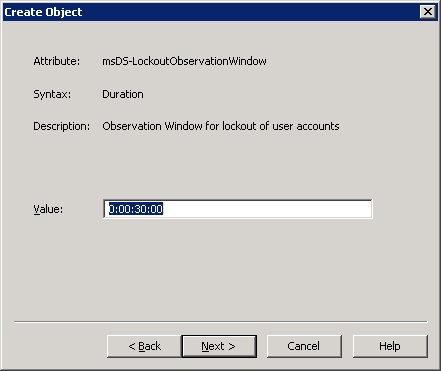
16. For the msDS-LockoutObservationWindow, enter amount in Time should pass before the User automatically gets “unlocked” in active directory. In this example we will set this amount to 30 minutes, 0:00:30:00, and then click Next.
17. For the msDS-LockoutDuration sets the duration that an account should be locked out in case of exceeding wrong password retrials. We will set this to the same duration as the previous setting.
18. Click Next and Finish, the wizard should successfully close if all parameters are entered correctly.
19. We now have a PSO created and ready. We now need to apply this PSO to a certain amount of users or groups.
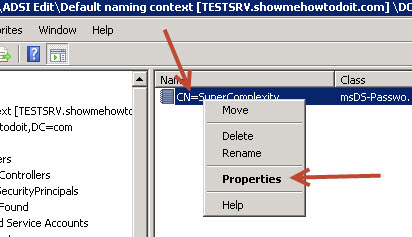
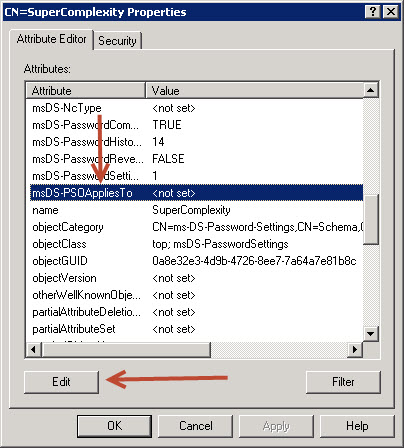
20. Right-click on freshly created object in the console tree, in our case CN=SuperComplexity and then select Properties.
21. Scroll down to the attribute msDS-PSOAppliesTo and press edit.
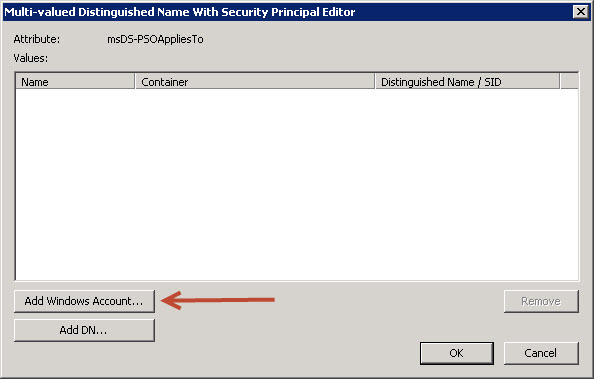
22. On the newly opened screen, press “Add Windows Account…”.
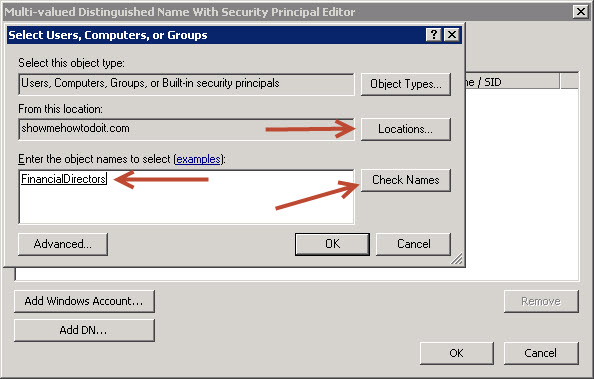
23. Now you may add individual users or groups to the specific PSO. In this example, we have created a Global Security group FinancialDirectors and added a few users as members.
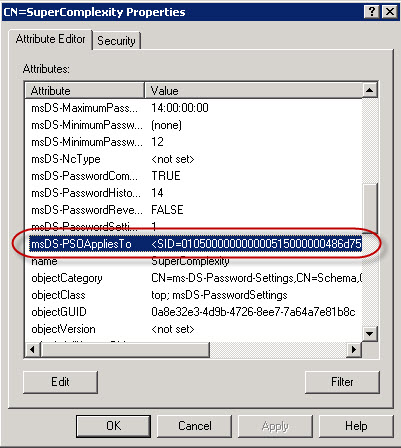
24. Press OK, OK and Apply, and verify that the msDS-PSOAppliesTo attribute contains a SID value. If the value field stays unconfigured, scroll down to the Considerations section.
25. Done! Next time a user needs to change password, the above PSO will be in effect. If you need to deploy immediately the PSO, just go to Active Directory Users and Computers and select “User must change password at next logon” under User properties.
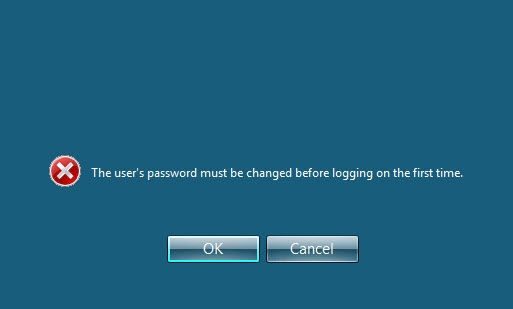
26. If you try to logging on with an account that has expired password or a newly created account, you will be prompted to change the password
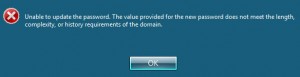
27. The user we are trying to logon belongs to the group FinancialDirectors, therefore the password complexity requirements are those of SuperComplexity’s policy. Trying to set as password P@ssw*rd should not work, not because of complexity, but the password length requirements (12 characters long).
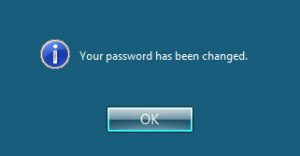
28. Trying to re-set the password P@ssw0rd2012 should be OK.
Considerations
- Both Forest and Domain functional level must be set to 2008 level for fine-grained password policy to function.
- If you have deployed multiple PSOs applied and want to check which PSO applies to specific user, you may use the following command: dsget user
-effectivepso - Fine grained password policies do not interfere with custom password filters that you might use in the same domain.
- If you have deployed custom password filters to domain controllers running Windows 2000 or Windows Server 2003 you can continue to use those password filters.
- If the user does not have any PSOs directly or indirectly linked through group membership, the Default Domain Policy is applied.
- Password complexity errors on Windows XP® client computers: When a user to whom an FGPP applies attempts to change his or her password on a client computer that is running the Windows XP operating system, an error message appears, informing the user that the new password does not conform to the settings that are defined in the domain policy, instead of informing the user that the new password does not conform to the settings that are defined in the FGPP. You may ignore this message and assume the required settings are the ones defines in the PSO.
References
AD DS Fine-Grained Password and Account Lockout Policy Guide by Microsoft.
http://technet.microsoft.com/en-us/library/cc770842%28v=ws.10%29.aspx
ADSI Edit
http://technet.microsoft.com/en-us/library/cc773354%28v=ws.10%29.aspx
Fine-Grained Password and Account Lockout Policy Review
http://technet.microsoft.com/en-us/library/cc754544%28v=ws.10%29